EBS is now the Gold Partner of Stratus Technologies & the Value-Added Reseller of eG Innovations
Forcepoint was created to empower organizations to drive their business forward by safely embracing transformative technologies – cloud, mobility, Internet of Things (IOT), and others – through a unified, cloud-centric platform that safeguards users, networks and data while eliminating the inefficiencies involved in managing a collection of point security products.
With the strong partnership with Forcepoint, EBS will further leveraging our professional expertise in project management, delivering distinct advantage and greater value to our customers.
Knowledge DeliveryWhat is APT ?An advanced persistent threat (APT) is a set of stealthy and continuous computer hacking processes, refers to Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information. APT signifies sophisticated techniques using malware to exploit vulnerabilities in systems, an external command and control system is continuously monitoring and extracting data from a specific target. The purpose of attacks is to place custom malicious code on one or multiple computers for specific tasks and to remain undetected for the longest possible period.
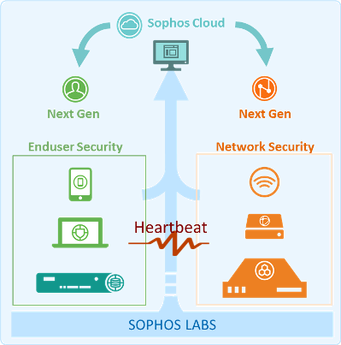
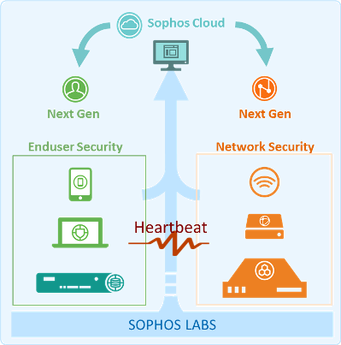
Sophos First to Bring Synchronized Security to Endpoints and Networks
Shares intelligence in real time across a trusted channel between your endpoints and your firewall
more effective protection against advanced malware and targeted attacks
Accelerated discovery of advanced threats
Sophos Firewall OS instantly and automatically communicates to the suspect system exactly what the firewall is detecting
The Sophos next-gen endpoint protection agent immediately uses that information to discover the process behind the threat.
Active identification of compromised systems
Offers firewall all the information you need to respond quickly: the name of the computer that’s misbehaving, the user who’s logged in, and the file path of the process that’s sending malicious traffic.
Automated incident response
Automates the important step of isolating compromised endpoints.
instantly applies a customizable policy to restrict or isolate infected systems.
Instant visibility into endpoint security status
A simple red, yellow, or green indicator lets you know in real time, which systems require immediate attention, which can be addressed at your convenience
Accelerates applications while making storage environments easier to manage
- Accelerate critical applications with the scalable performance of IBMR Flash Core? technology.
- Deploy all-flash storage for less than the cost of hard-disk drives (HDDs) with IBM Real-time Compression
- Harness the power of data using storage virtualization powered by the ultra-low response times of IBM Micro Latency?
- Accelerate time to value with agile, easy to- implement, fully- integrated systems
- Protect your data with a full suite of disaster-recovery tools including snapshots, clones and replication
- Achieve advanced virtualization, provisioning and performance management with IBM Virtual Storage Center
Palo Alto WildFire
APT Prevention technology – Protection from targeted and unknown threats
Once a file is deemed malicious, WildFire automatically generates protections that are delivered to all WildFire subscribers within an hour of detection. A WildFire license provides your IT team with a wealth of forensics to see exactly who was targeted, the application used in the delivery, and any URLs that were part of the attack.